Time and again, it has been proved by hackers that no system is perfect enough to prevent a cyberattack. IT giants like Microsoft, Facebook, Twitter, etc. have been targeted repeatedly by hackers to prove that every system has loopholes that can be exploited by these cyber crooks to gain unauthorized access. Security is the new buzzword of the IT industry. Online customers closely monitor the security measures adopted by stores. Magento stores are the latest targets of these crooked geniuses as it powers around a quarter million websites around the globe. Hackers have been trying to besiege Magento stores to manipulate the in-built scripts used for payment transfer. This new threat is aptly called Magento Killer by the experts. Let us see why magento hire developer well-versed with security features for configuring its platform?
Magento Killer – A Preamble
This malevolent PHP script tries to beleaguer Magento stores by altering the payment-related data in a system table core_config_data. As the name suggests, it doesn’t kill the Magento store. The compromised Magento store under attack would continue to function, but the script opens a backdoor to the Magento store through which the data in core databases are compromised. This vulnerability, if not resolved swiftly, can lead to the demise of the Magento store.
Countries Targeted By Magento Killer
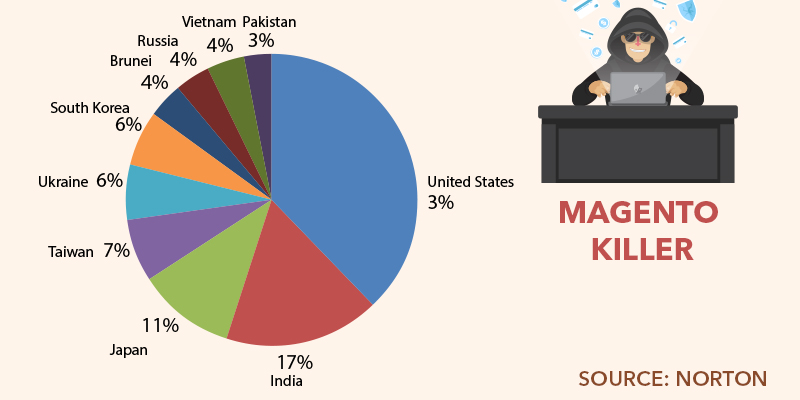
The US Magento stores are a prime target for hackers using Magento Killer. The market share of Magento is around 24% in the US which is the obvious reason for the attack. Around 38% of Magento Killer attacks were targeted at US-based Magento stores. The US Magento stores are closely followed by the online stores in India, the hub of shopping frenzy customers. The reason for targeting Indian stores is the lack of security measures adopted by India-based online companies. The following diagram gives us a picture of the countries in this undesirable list of Magento Killer hackers.
Malicious Operations Performed By Magento Killer

In the preliminary phase of attaching, Magento Killer, also known as $ConfKiller, uses SQL queries encrypted in base64. These special queries are written to target two objects named Update DB (Savecc) and Update PP(MailPP). These objects facilitate these black hats to embezzle the payment data and shift it to any location of their choice. The Update DB object, once under siege, configures the Magento store to collect credit card data to save it locally, instead of sending it to the desired payment gateway. The other object, i.e. Update PP can aid the hacker in setting up his own PayPal account as the beneficiary of the business transactions in place of the merchant’s. The Magento stores the credit card data of customers in encoded form but the Magento Killer script lets the hacker steal the encoding key from ./app/etc/local.XML file to decode the credit card information. As a result, the payments done would reach the attackers instead of the merchant. Apart from this, the customers’ personal information is now on sale on the darknet, leaving him vulnerable to a volley of cyberattacks. Instead of going through this unfortunate series of events, best hire magento developer to counter the security risk.
Security Measures To Be Adopted

There are some smart hacks to prevent a Magento store from this Killer script. The first one is to always use the latest version of Magento as the newer versions are more secure than, the earlier versions. Installing a Web Application Firewall would be another wise step to safeguard the valuable customers’ data as it adds another layer of security to an online store. Two-step authentication is the need of the hour in all payment transactions. In layman’s terms, only password and user ID are not enough to log in to the system. It should be succeeded by a one-time code sent on the user’s email id or mobile phone, for logging into the system. The website should be regularly audited by security experts to detect a potential security threat. A secure server should be used for hosting a Magento store to add extra protection. Apart from this, in the event of a customized Magento store, Magento’s best development practices should be followed.
Wrapping Up

Although Magento is otherwise a secure platform, it has been targeted lately by crackers to exploit a vulnerability in its system. This Magento Killer threat manipulates the default payment process to route the customer’s payment in their account instead of the merchants. The Magento stores should be vigilant about the security of their websites. The Magento Killer threat can be tracked by regular security audits. Once tracked, cybersecurity experts should be hired to tackle the menace.



